A Real-World Case Study in SD-WAN Diagnostics
It started like many support tickets do—a reseller flagged an issue with one of their clients experiencing connectivity instability. The end user (EU) had been suffering from intermittent internet dropouts and complete loss of connection to the rest of their SD-WAN network. At first glance, it seemed like a standard case. But what unfolded revealed a cautionary tale that every IT manager, reseller, and business owner needs to hear.
Standard Diagnostics, Unusual Symptoms
Our Level 1 diagnostics quickly revealed something unusual—unexpected CPU usage spikes on the SD-WAN node. While the reseller proceeded to replace the node as a precaution (suspecting possible hardware failure), our team dug deeper. The new node was deployed. The issue persisted. That told us everything: The problem wasn’t with the node. It was something external.
Chasing Ghosts

Noticing high CPU usage correlated with massive connection tracking (conntrack) table spikes—a classic sign of overload. Hard Caps were imposed to keep the CPU from being overwhelmed and packet captures launched to identify what was flooding the system.
The captures? Almost silent.
Traditional tools failed us. It was like a DDoS attack coming from inside the building.
Let there be Light!
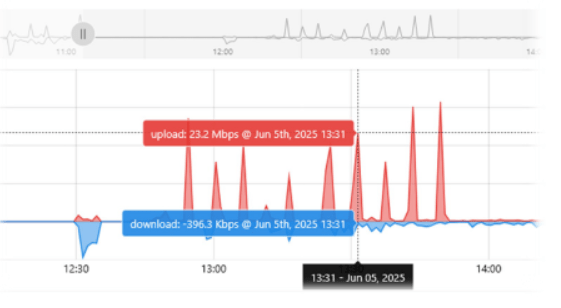
While traditional diagnostics revealed little, our engineers noticed unusually high outbound data usage patterns in Antares, our real-time analytics and telemetry dashboard. This anomaly of large volumes of sustained uploads from a single internal IP didn’t match typical client
Closing In!
This triggered a deeper inspection using DPI Data(Deep Packet Inspection) via Illuminate, allowing us to correlate the timestamped data with specific traffic patterns. That’s when the truth surfaced: the traffic was originating from an NVR, which had been compromised and was silently exfiltrating sensi-tive footage to a Russian IP via Brazil.
An infected NVR (Network Video Recorder) inside the client’s network.
It had become part of a botnet—exfiltrating 36.6 GB of video footage from a Medical Centre over just 48 hours, routed through Brazil and uploaded to a Russian IP.
Hands to Action!

The rogue NVR was immediately blackholed and quarantined. But the implications were sobering.
In many regions, incidents like these are legally reportable data breaches. And think about this:
Could your image, personal records, or financial details be visible in the footage of a compromised surveillance system?
With HD cameras now ubiquitous across retail, healthcare, public transport, and corporate offices, video data is fast becoming one of the most overlooked cybersecurity risks.
Key Takeaways for IT and Security Teams:

- Regular endpoint monitoring isn’t enough—you need visibility at the network edge.
- Surveillance systems are often the weakest link—treat them as critical assets.
- Traditional tools may not catch stealthy threats—behavioral analytics and telemetry are essential.
Is your organization prepared to detect and stop internal DDoS-style behavior before it becomes front-page news?
At a time when video is data—and data is gold—it’s not just your files that need protection. It’s your audio, your images, and your cameras too.
contact@nepeannetworks.com | nepeannetworks.com
If you found this insightful, feel free to connect or share. Let’s keep the conversation going around securing the networks of tomorrow—today.
#CyberSecurity #SDWAN #IoTSecurity #NVR #DataBreach #NetworkForensics #LinkedInTech #InfosecNepeanNetworks


