Overview
In June 2022, a large IaaS (Infrastructure as a Service) provider—one of Nepean Networks’ resellers—was hit by a devastating ransomware attack that encrypted every piece of data they hosted: client files, workstations and servers.
What followed was a business nightmare… and a critical test of resilience.
The Incident: One Morning Changed Everything
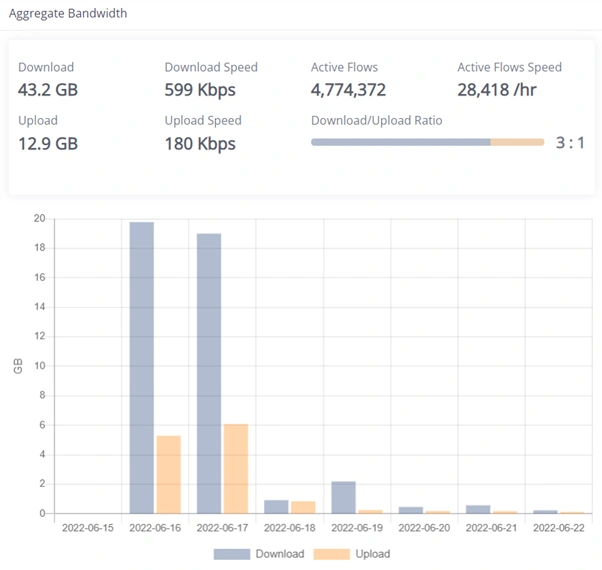
At 4:45 AM, malicious code executed within the provider’s environment and quickly “phoned home” to a command-and-control server hosted in the U.S.
Moments later, ransomware began tearing through the network, encrypting everything it touched. Hours later, it was all over. The damage was done.
The provider—fast asleep—was jolted awake by calls from panicked clients. Virtual desktops were unreachable. Exchange email wasn’t syncing. Applications were failing.
Logging into their core infrastructure, the horror became clear: The entire VMWare environment was gone.
The Gut Punch: No Backups. No Way Out.
As their teams scrambled to lock down systems, find the infection source, and restore services, the realization hit like a truck:
“We never set up offsite backups. Everything—everything—was on the same hypervisor. It’s all encrypted.”
No usable client data. No backups. Years of trust, business, and infrastructure—wiped out in minutes.
The Investigation Begins
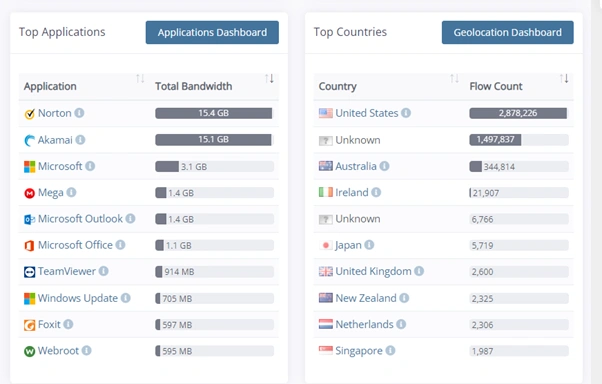
Rebuilding from scratch was the only option.
Clients demanded answers (many of whom were Law Firms). A third-party cybersecurity team was brought in to investigate. But they were flying blind:
- No perimeter firewall
- No usable logs
- Only OS-level software firewalls
What they desperately needed:
- Forensic insight
- Data flow history
- Proof of whether customer data had been exfiltrated
The Turning Point: Enter Nepean Networks and Illuminate
Just one week earlier, the provider had deployed Nepean Networks’ Illuminate — a firewall-independent L7 Deep Packet Inspection (DPI) analytics tool.
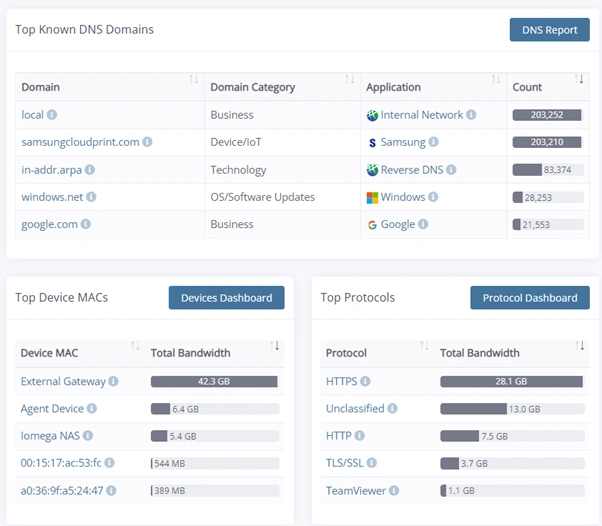
This changed everything.
- With Illuminate’s visibility, the cybersecurity team could:
- Trace every historical data flow
- Identify the exact command and control server IP and Host
- Monitor all pre and post-infection traffic
- Pinpoint where the encryption key was sent (Megashare, New Zealand)
- Most importantly: confirm no customer data left the premises
That final insight saved the provider from prosecution — and likely the business itself.
Rebuilding: From Chaos to Resilience
Although many clients were lost, enough remained to rebuild.
With Nepean’s help, the company transformed its approach:
- Security-first architecture
- Segmented, monitored, and protected ingress/egress points
- Cloud and on-prem environments protected with vendor-agnostic tools
Key Takeaway: Visibility Saves More Than Logs Ever Will
Many MSPs chase the dream of an all-in-one vendor: one box that handles routing, firewall, and analytics. But when disaster strikes, that’s a single point of failure.
Nepean’s model separates these layers—network, security, and visibility—giving MSPs freedom to choose best-of-breed solutions and retain independent analytics across all vendors.
The result?
An unbiased, always-on, retroactive lens into your network. Illuminate delivers the “extra set of eyes” every MSP needs—before, during, and after an incident.
Request a Live Demo
If you’re an MSP or IT professional looking to protect your clients—and your business—get a firsthand look at what Illuminate can do.


