Advanced Traffic Visibility
What is Illuminate?
Business threats come in many forms, from Ransomware, Covert Surveillance or simply from disgruntled staff stealing company data.
Your employee just upload 20GBs of company data to Dropbox. Your CCTV system is compromised and sending video traffic internationally. Would your firewall block that traffic? The answer is NO.
Firewalls are only a small part of an overall security framework and struggle to provide real-world insights that are meaningful to human interpretation.
Illuminate provides alerts and insights which are easy enough for a business owner to understand, yet detailed enough for the most senior technicians to work effectively.
Threat Detection
Identifies security threats to the organization by analyzing packets in real time.
Network Performance
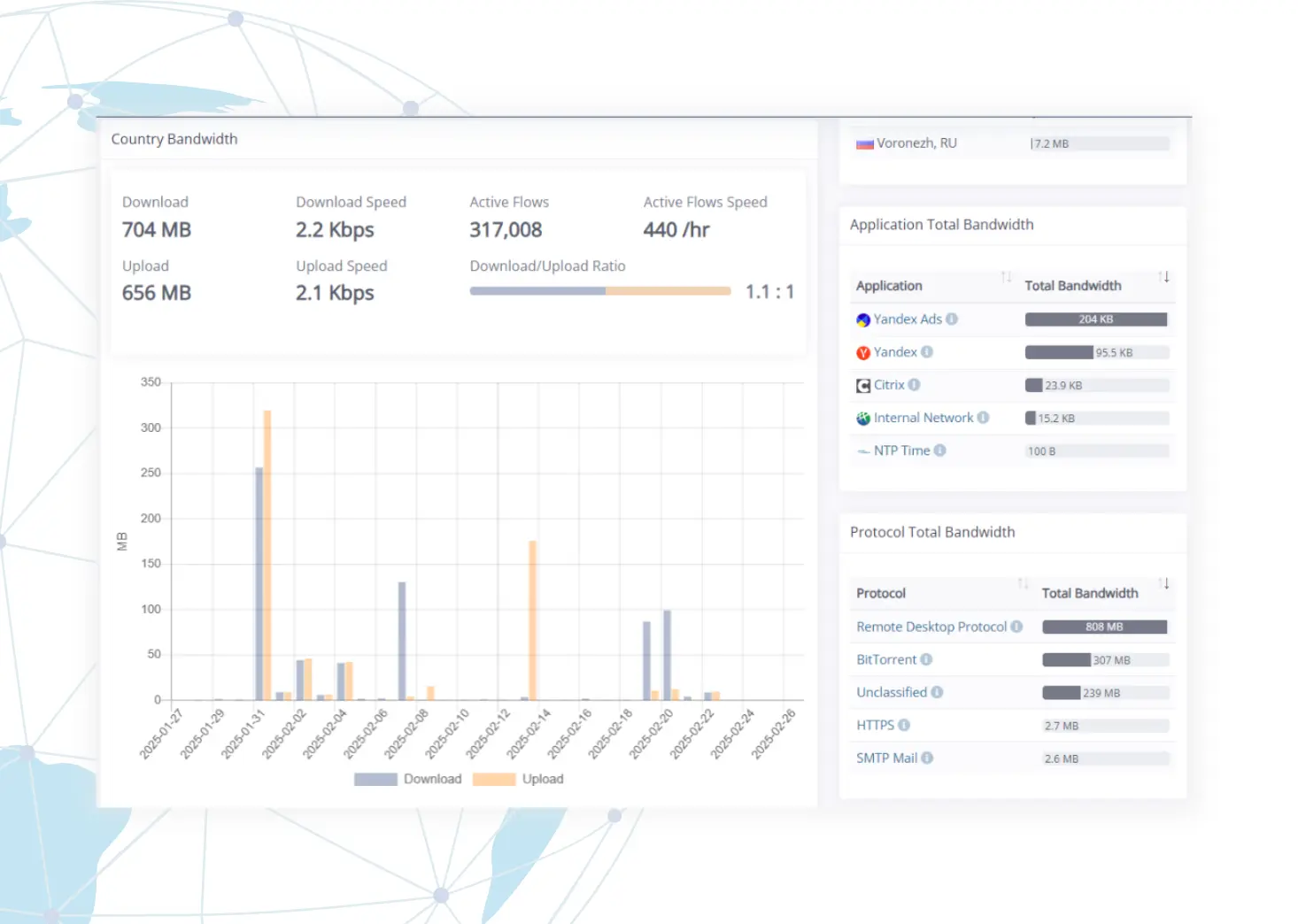
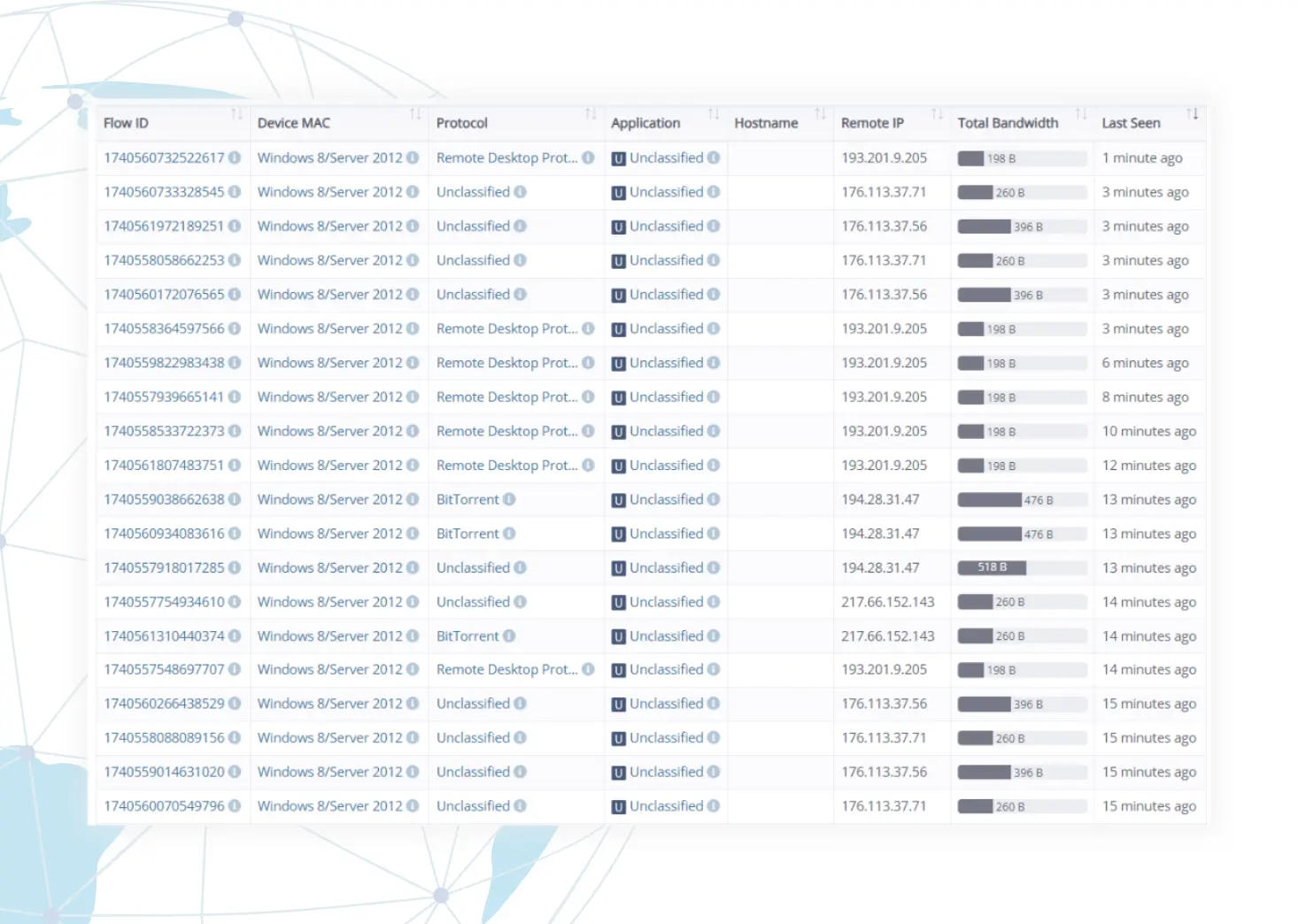
Pinpoint the source of bandwidth hogs. Use the data to craft QoS policies or to justify why additional bandwidth should be procured.
Security Incident Analysis
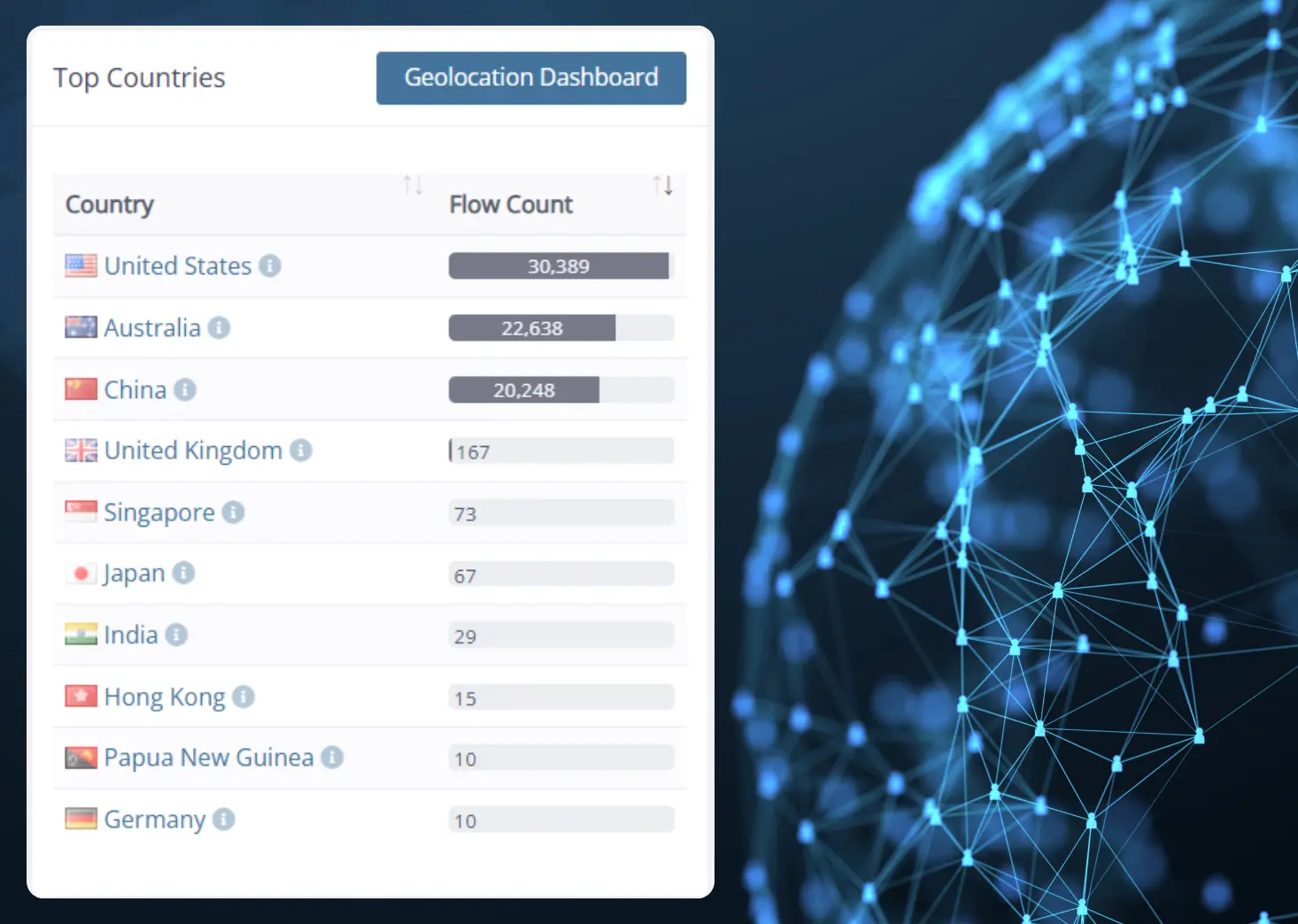
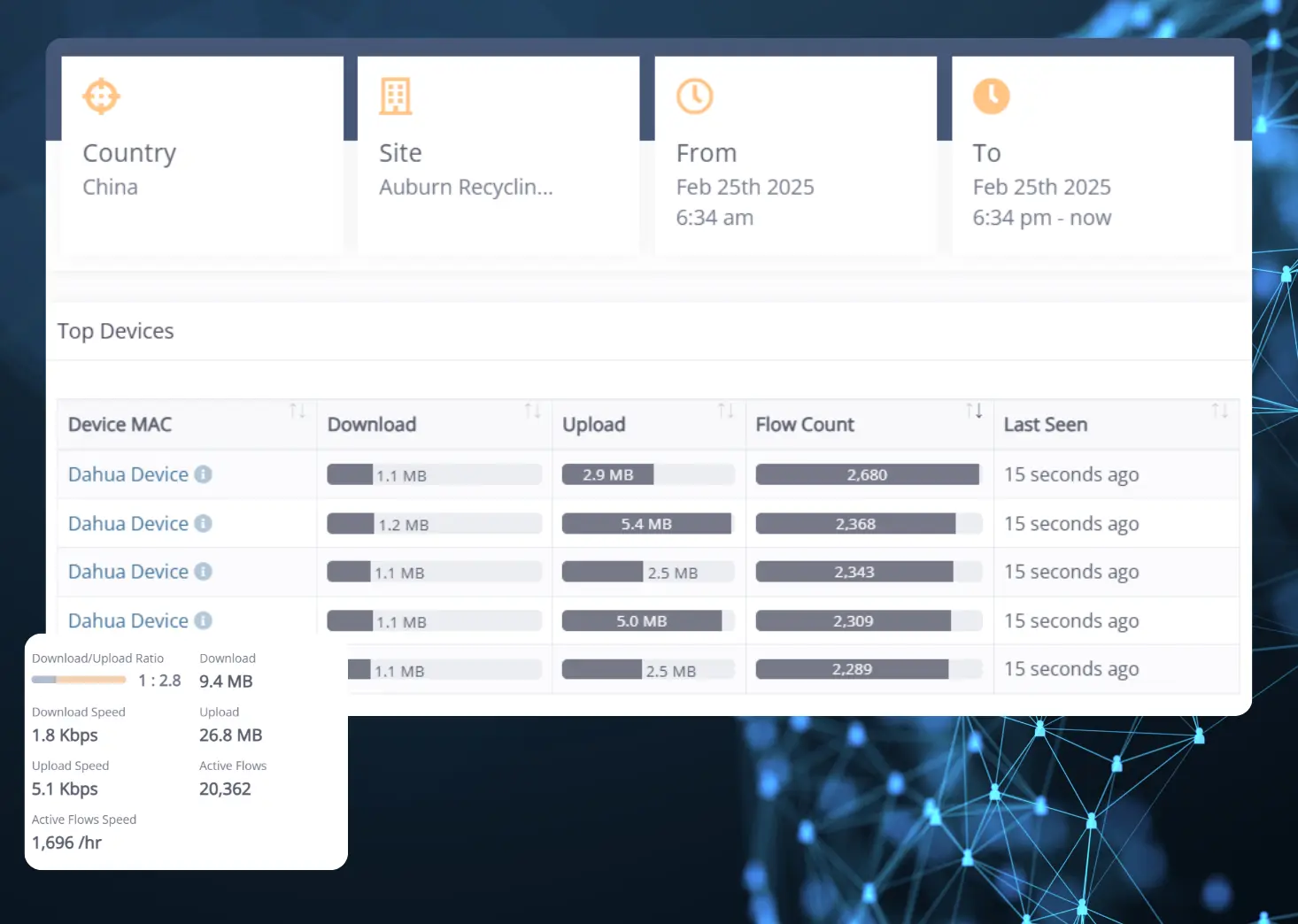
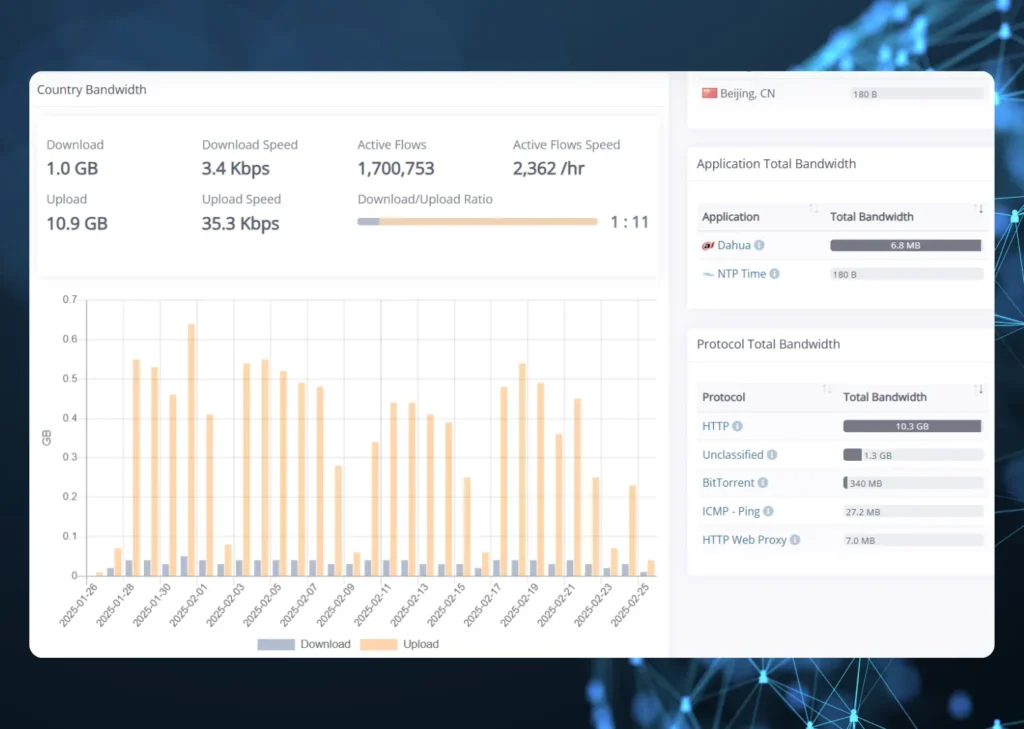
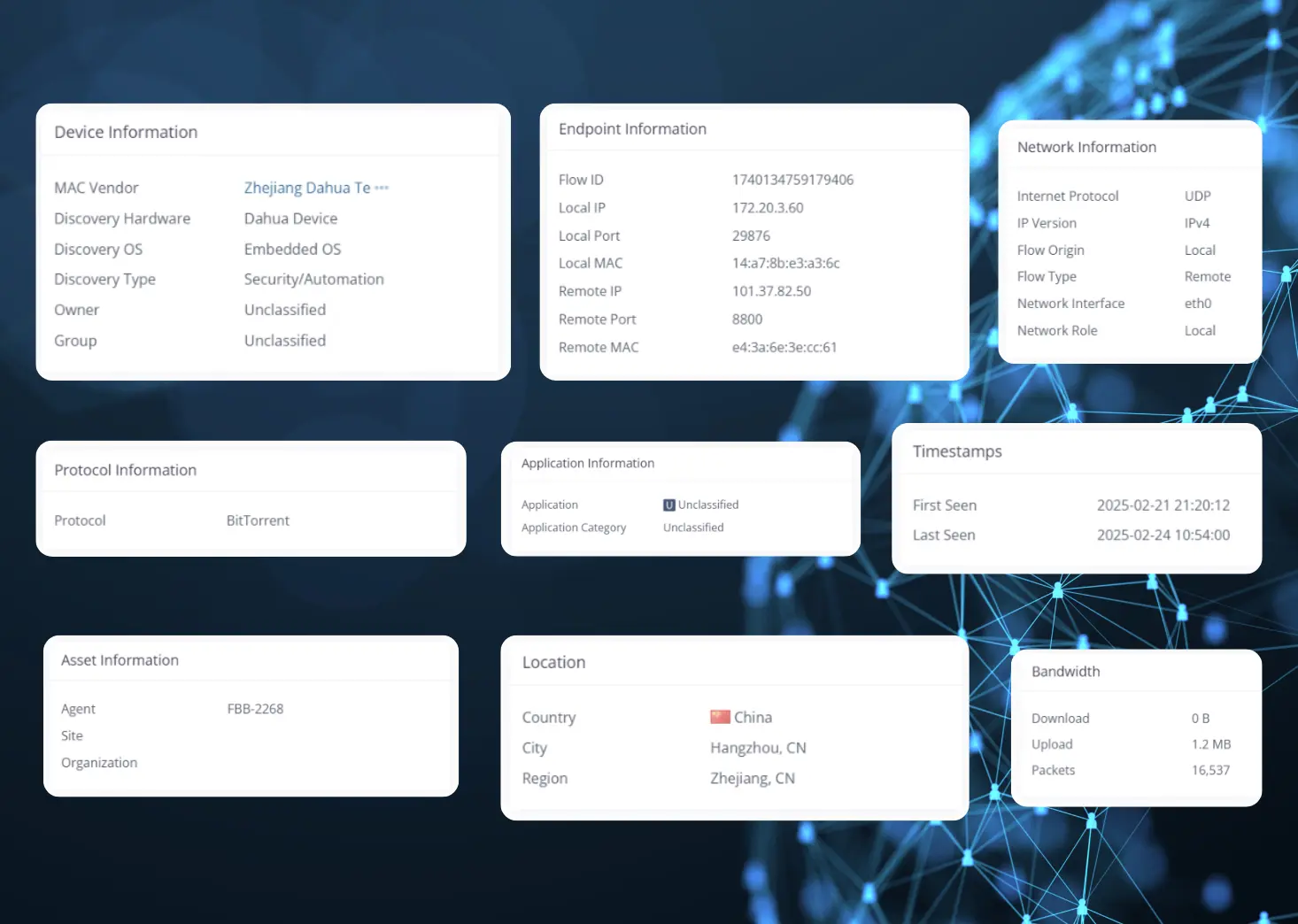
1. CCTV DataUpload to China
Detecting High Traffic Levels
Network monitoring reveals an unusual spike in outbound traffic to China. The volume of data being transmitted is significantly higher than expected for normal operations. This raises concerns about potential data leaks or unauthorized access.
Identifying Internal Devices
Suspicious Upload Activity
Investigating Recorded Flows
Firmware-Driven Traffic
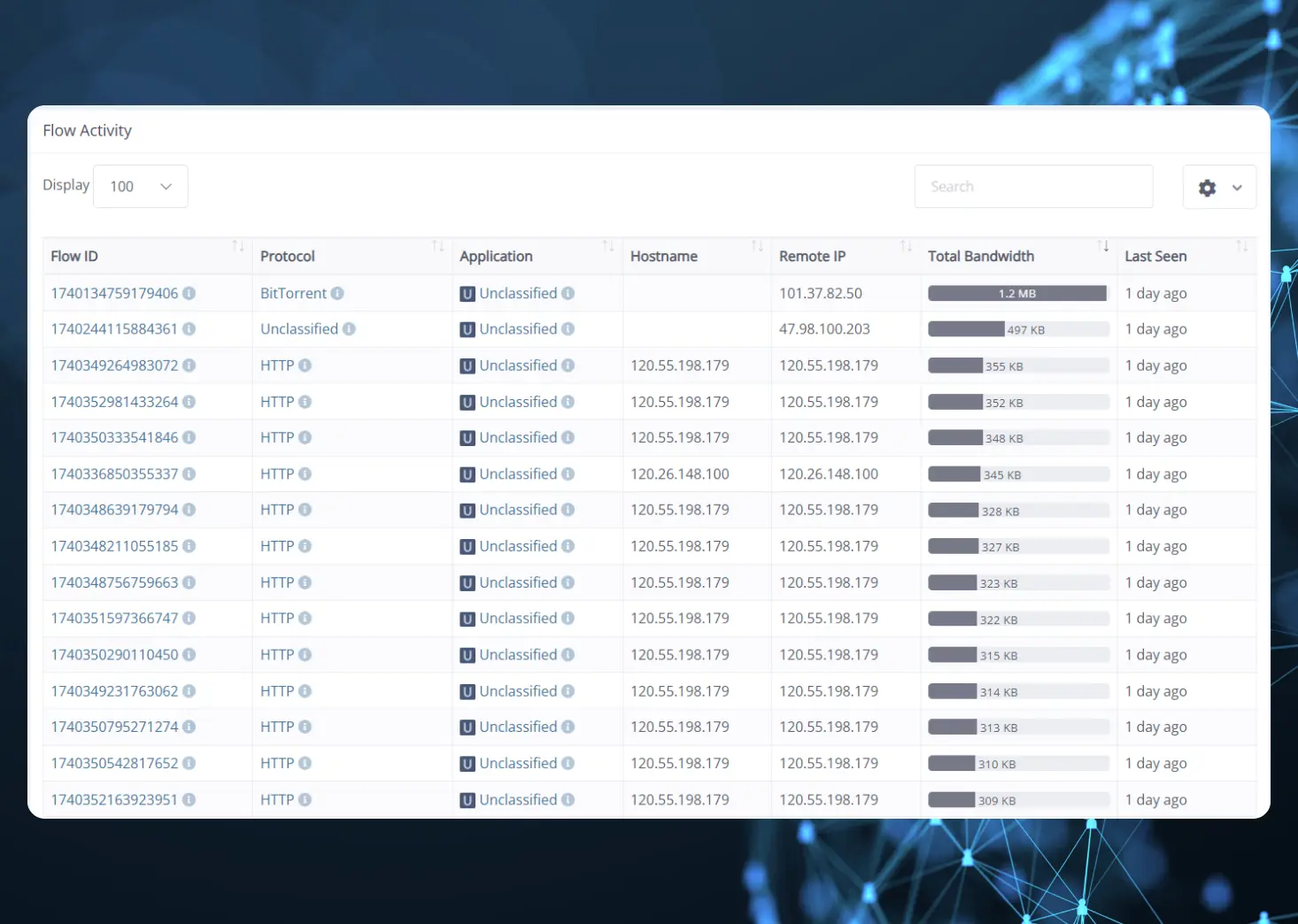
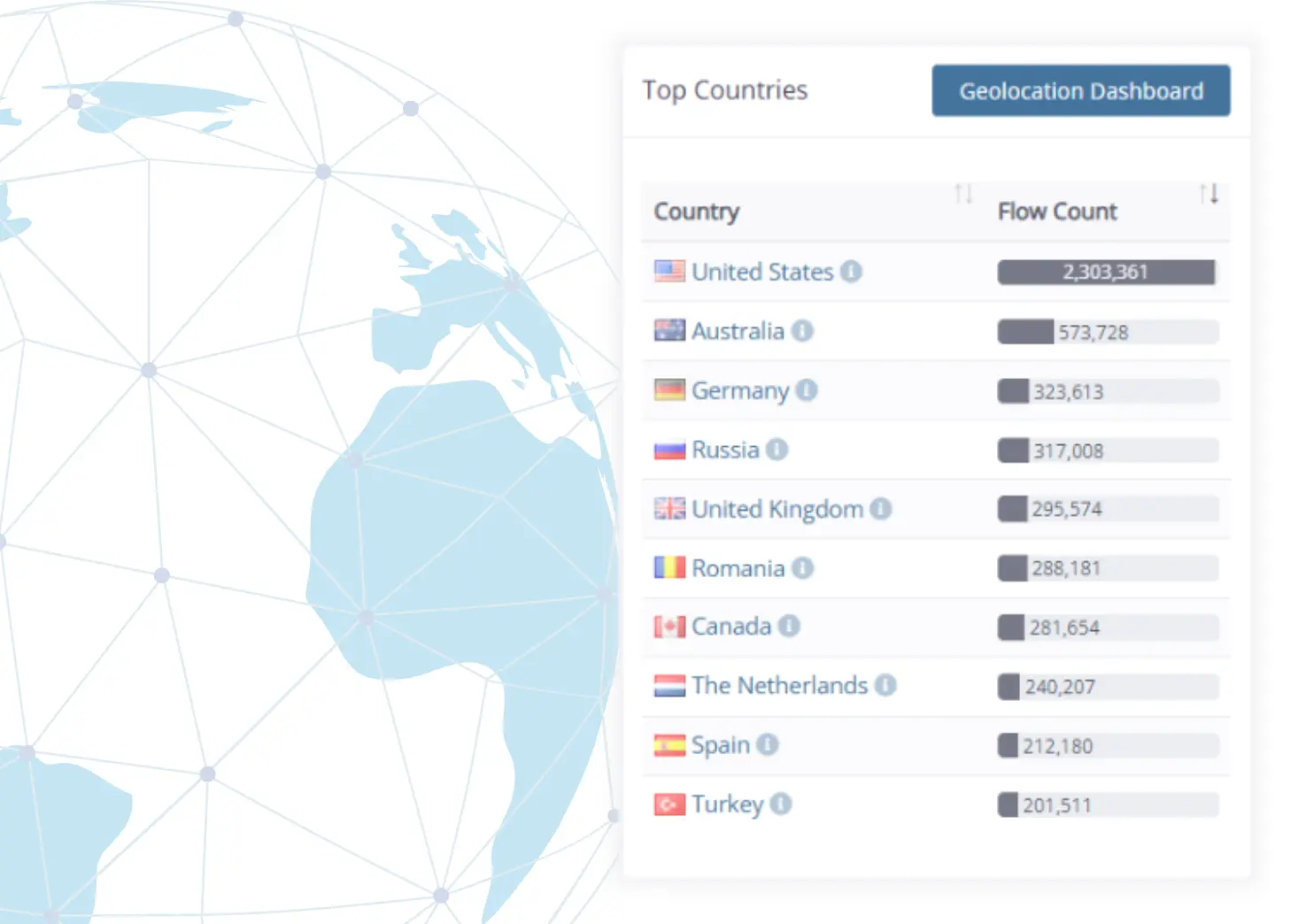
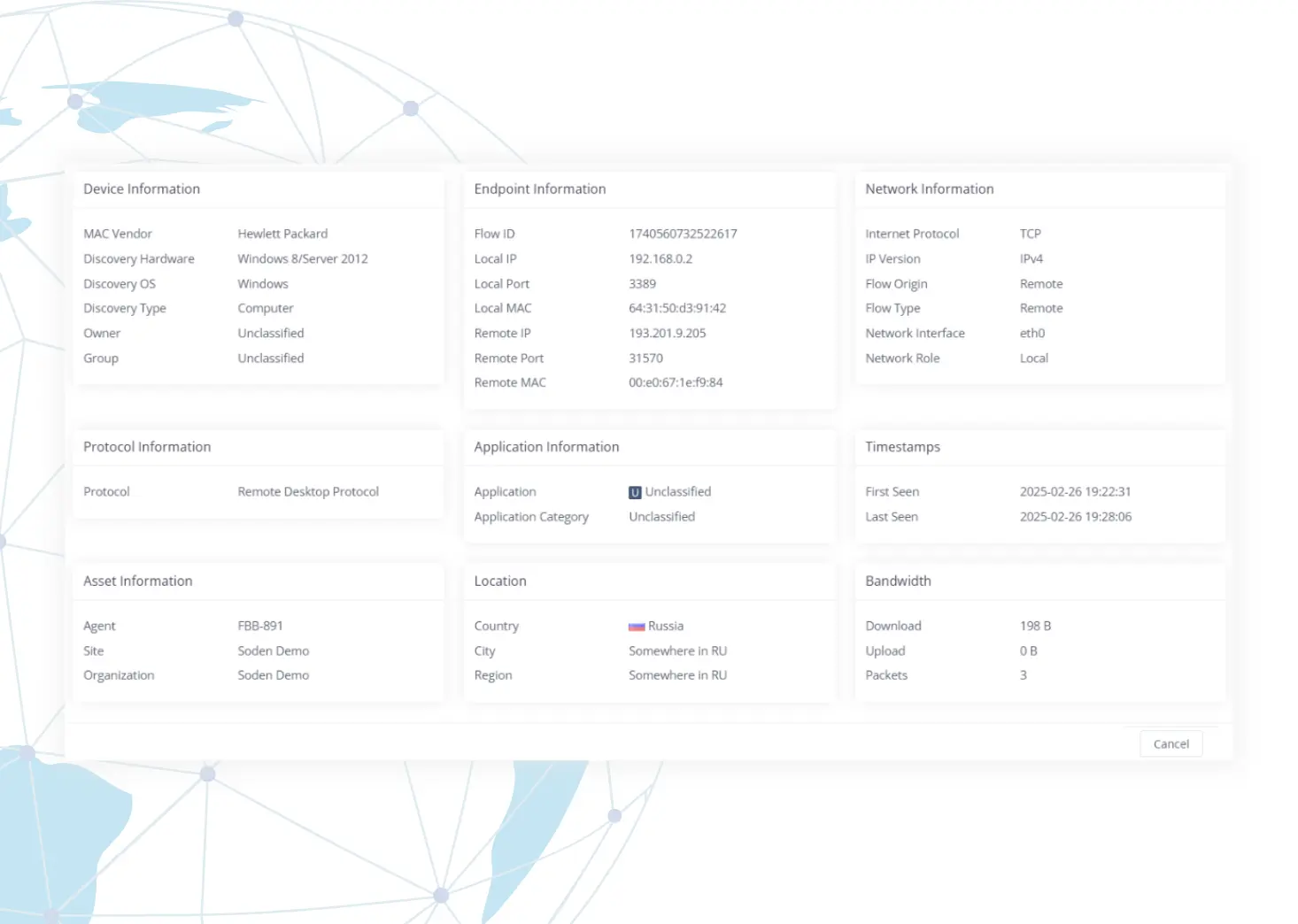
2. RDP Brute Force Attack Analysis
Detecting Unusual Russian Traffic
Remote Desktop Attacks
The traffic is classified as Remote Desktop Protocol (RDP) traffic. A total of 440 connection attempts per hour are detected. This suggests a possible brute-force attack targeting remote access credentials.
Analyzing Ongoing Attempts
Tracing the Attack Source

Nepean Networks SD-WAN L7 DPI Analytics
Go beyond traditional monitoring and gain real-time visibility into application performance with Layer 7 Deep Packet Inspection (DPI) analytics.
Benefits of DPI Analytics
Real-Time Insights
Gain deep visibility into network traffic, application usage, and potential security threats.
Security Compliance
Detect anomalies, prevent data breaches, and ensure compliance with industry regulations.
Speed Optimization
Enhance traffic management and resource allocation for a seamless network experience.
Ready to Transform
Your Network?
Discover how SD-WAN can revolutionize your business. Book a demo with our experts to see the technology in action and explore tailored solutions for your needs.